Let's be honest - dev environments are a nightmare. I've wasted way too many hours on "works on my machine" bullshit. VS Code Dev Containers fix this by shoving your entire dev setup into a box that works the same everywhere. No more "install Node 18.2.0, not 18.3.0 because that breaks the crypto module and you'll get MODULE_NOT_FOUND errors."
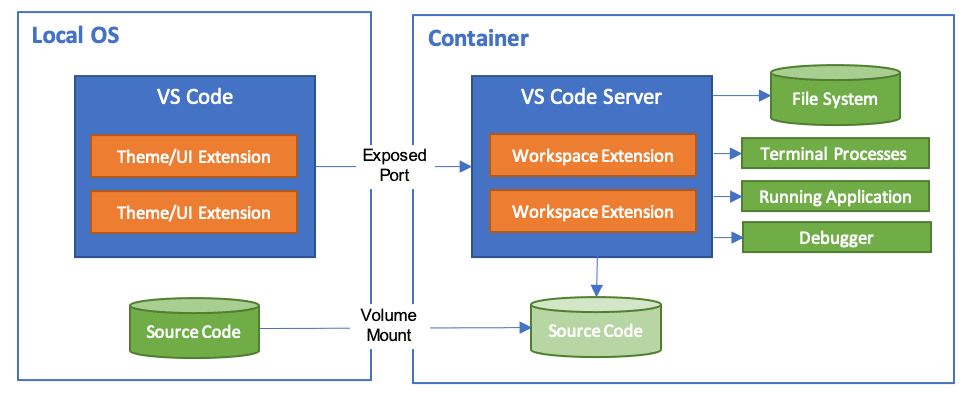
The traditional "works on my machine" problem just became "works in my container," which is actually an improvement. GitHub moved to Codespaces because they got tired of new hires spending three days installing dependencies. Now onboarding takes 30 minutes instead of 3 days copying random commands from Stack Overflow threads titled "npm install failing with EACCES permission denied".

The Team Collaboration Revolution
Containers solve the real problem: environment drift. You know how your team has one person whose setup works perfectly and everyone else's environment is subtly broken in different ways? Containers fix that by making everyone's environment exactly the same. No more "can you send me your .bashrc?" in Slack channels.
Teams can share entire development contexts - not just code, but databases, services, debugging configurations, even that weird legacy SSL certificate your app needs that throws `certificate verify failed` errors. Big teams figured this out first because they couldn't afford to have developers debugging environment issues instead of building features.
This approach works especially well for:
- Cross-functional teams where frontend devs need to spin up the backend without understanding Docker
- Remote teams where "it works on my machine" becomes "it works in my home office but not yours"
- Enterprise environments where IT mandates specific security tools that break half the normal setup guides
- Open source projects where contributors give up after failing to get the project running locally
Enterprise Adoption Patterns
Big companies do this because their environments are hell without containers. The smart ones start small - pick one frustrated team, get them working, then expand. The dumb ones try to containerize everything at once and create a bureaucratic nightmare. I've seen teams where gradual adoption works way better than mandating containers company-wide on Monday morning.
The enterprise workflow that actually works:
Phase 1: Find the Most Frustrated Team (1-3 months)
Start with teams already struggling with environment issues. Focus on proving the concept works for your specific setup and security requirements. Don't try to solve every possible use case.
Phase 2: Create Templates That Don't Suck (3-9 months)
Document what worked. Create base images that other teams can actually use. Train internal champions who can help other teams instead of creating support tickets for the platform team.
Phase 3: Integration Hell (9+ months)
Integrate with CI/CD, security scanning, and whatever internal platforms your company insists on using. At this stage, container creation should be under 5 minutes and most environments should work consistently. 99% consistency is bullshit - aim for "works most of the time."

Real-World Team Collaboration Benefits
The collaboration benefits go beyond technical consistency. When someone reports a bug, you can spin up their exact environment in 2 minutes instead of playing "I can't reproduce this" ping-pong for a week while the bug burns money in production.
Knowledge Transfer Actually Works
When senior developers create dev container configurations, they're packaging years of hard-won environment knowledge. New team members get access to optimized tooling, ESLint rules that don't suck, Prettier configs that match the team style, TypeScript settings that actually work, debugging setups that connect on the first try, and database states with realistic data. No more spending weeks recreating the perfect development setup that took the senior dev 3 years to build.
Cross-Team Collaboration That Doesn't Require Meetings
Teams working on microservices can share development environments using Docker Compose that include all service dependencies. Frontend teams can spin up a complete backend environment without having to understand how the auth service works or why it needs PostgreSQL 13.8 specifically (because 14.x breaks the custom extensions). Kubernetes integration through Skaffold and Tilt makes this even better when it works, which is about 80% of the time.
Security Teams Actually Like This
Enterprise security teams love dev containers because they can audit exactly what tools developers are using instead of discovering random shit installed via `curl | sudo bash`. All tools and dependencies are declared and versioned. Many organizations find dev containers improved their security by eliminating shadow IT tools and enabling consistent security scanning across environments.
The Challenges Organizations Face
The biggest challenge isn't technical - it's developers who've spent years perfecting their setups and don't want to give up their custom .vimrc, seventeen terminal aliases, and that one weird PATH modification that makes their ancient Perl script work. I've watched senior engineers throw actual tantrums over losing their custom zsh prompt.
Don't try to containerize everything at once. That architect who mandated "all development must be containerized by Friday" spent the next month fielding angry developers who couldn't debug their applications anymore. Start with new projects where people haven't invested years in their local setup.
Performance Will Be Your Biggest Complaint
Container performance can be shit if you don't configure it right. File sync between host and container is painfully slow on macOS and Windows. Docker Desktop performance issues have over 1000 open GitHub issues for a reason - mainly because it turns your MacBook into a space heater while taking 3x longer to build than it should. GitHub Codespaces often performs better than local Docker Desktop, but it costs money and requires internet.
Cultural Wars
The biggest fights aren't about technical choices - they're about whether to include oh-my-zsh in the base image. I've watched teams split into factions over terminal configurations. The key is making containers feel like home instead of a sterile corporate-mandated prison. Allow customization where it doesn't break consistency.

Looking Forward: The Future of Collaborative Development
The trend toward development environment as code keeps accelerating. AI tools like GitHub Copilot, CodeWhisperer, and Tabnine work better in containers because they can understand the full development context - not just your code, but your toolchain, dependencies, and configuration.
The next evolution will probably be containers that automatically adapt based on what you're working on. Working on frontend components? Container automatically enables hot reloading and browser dev tools. Debugging backend services? Database tools and log analysis get priority. When it works, it'll be great. When it doesn't, you'll spend half your day fighting with containers that think they're smarter than you.
This represents more than just technological progress - it's enabling collaboration patterns that weren't possible before. But like most technological advances, it'll probably create as many new problems as it solves.