You know it's time for CloudBees when your Jenkins setup becomes that cursed box nobody wants to touch. Standard Jenkins scales like absolute shit - you'll start with one instance, then have 12 instances that nobody understands, then your builds randomly fail because someone updated a plugin on instance #7 and now the groovy.lang.MissingMethodException is haunting your build logs.
CloudBees CI is Jenkins for people who've been traumatized by watching one plugin update destroy everything at 2am on a Friday. Version 2.516.2.29000 dropped September 4th, and it actually fixes the stupid shit that made me want to quit DevOps and raise chickens instead.
The Real Problems CloudBees Solves
Community Jenkins plugins are a fucking security nightmare. Half of them haven't been updated since 2019, and the other half will throw java.lang.NoClassDefFoundError on Tuesday morning after you've had your coffee. CloudBees' Assurance Program means someone else deals with the plugin hell - they actually test this shit before it hits your production builds.
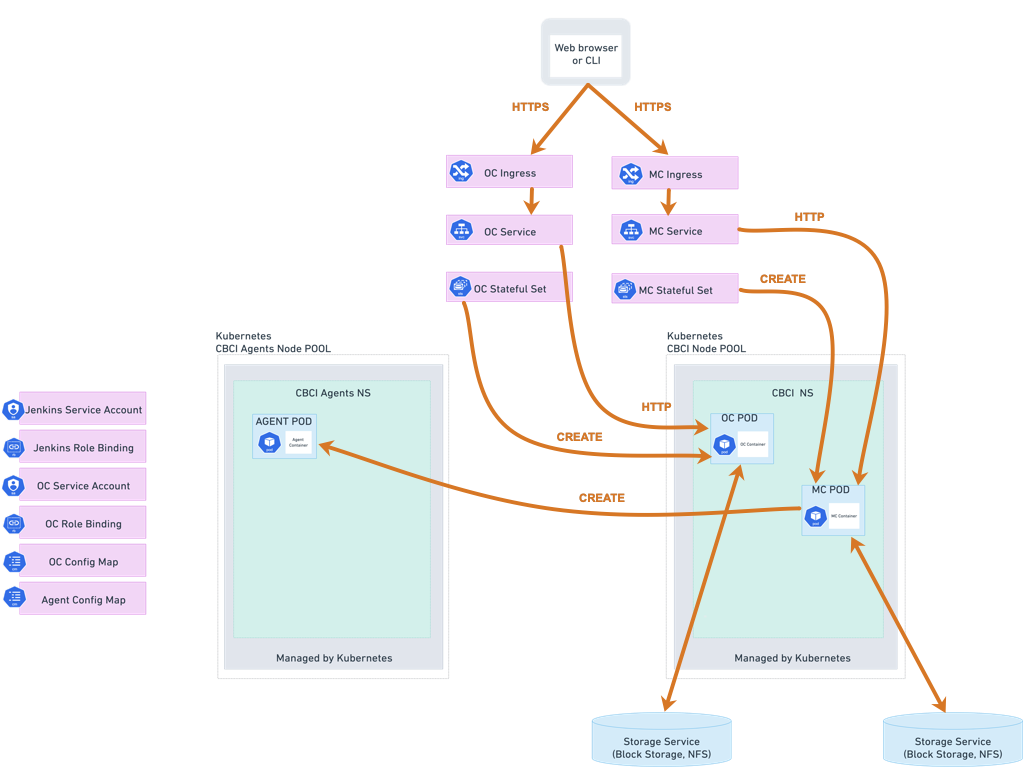
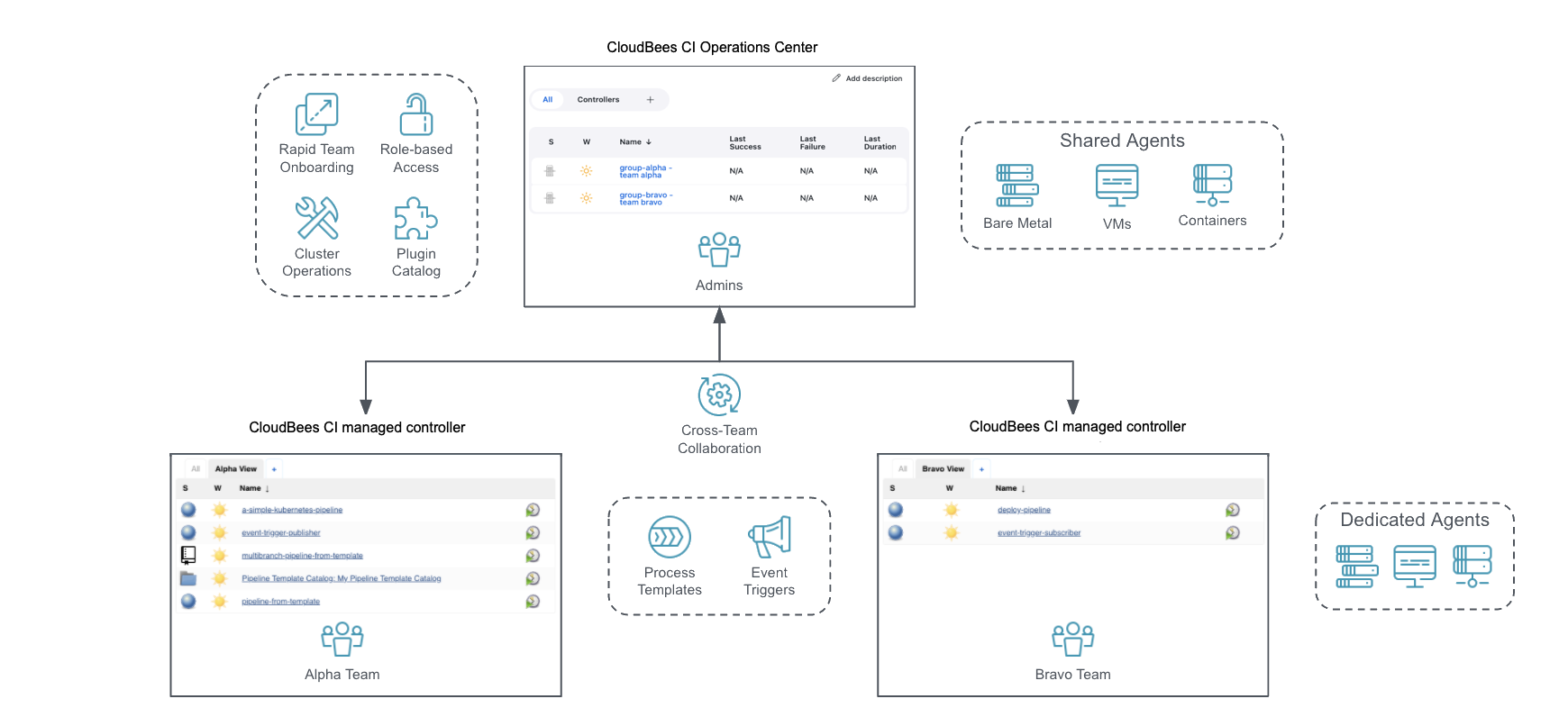
The ops center is basically Jenkins for Jenkins. Sounds ridiculous, but when you're managing 50 Jenkins instances and plugins break randomly at 2:47am, you'll understand why this exists. No more SSHing into 47 different servers to push config changes while your entire development team waits.
Configuration as Code means you can finally version control your Jenkins config instead of clicking through 47 different settings pages every time you need to recreate an instance. When your Jenkins box dies at 2am (and it will), you can rebuild from YAML instead of crying.
What Actually Works Different
High availability setup because Jenkins going down at 2am is not fun. Active-passive is cheaper, active-active costs more but your sleep schedule will thank you. When shit hits the fan, it automatically fails over instead of waking you up. Most of the time. Nothing's perfect, but it beats manually restarting Jenkins controllers while your dev team Slacks you angry face emojis.
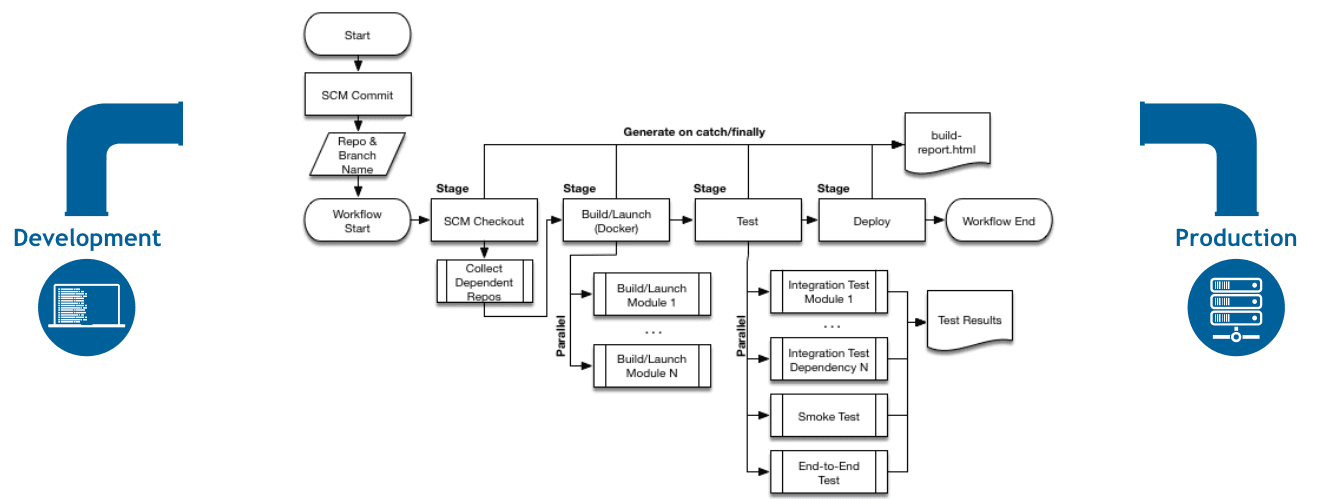
Pipeline templates stop developers from writing pipeline scripts that would make your security team quit. Standardized doesn't mean inflexible - teams can still do weird shit when they need to, but the basics are locked down so you won't get Permission denied (publickey) errors because someone hardcoded SSH keys.
The Forrester study claims 426% ROI and 99% downtime reduction. Marketing bullshit aside, if you're spending more hours unfucking Jenkins than building actual features, then yeah, throwing money at CloudBees starts looking smart.
But fixing the symptoms is just the first step. The real magic happens in how CloudBees redesigned Jenkins architecture from the ground up to actually work at enterprise scale.