I've audited enough Electron apps to know this shit is fundamentally broken. Your basic notepad app bundles the same browser engine that runs YouTube. Try explaining that to a security team without laughing.
The Audit Nightmare
Chrome has millions of lines of code that change constantly. Security teams take one look at it and give up. They flag it as "high risk - we're not auditing this garbage." The Chromium security team patches vulnerabilities constantly, and Electron inherits every single one.
When CVE-2022-29247 hit, renderers could access APIs they shouldn't have. We had to patch a bunch of apps - honestly lost count. The security team was freaking out because nobody knew which apps used what Electron features.
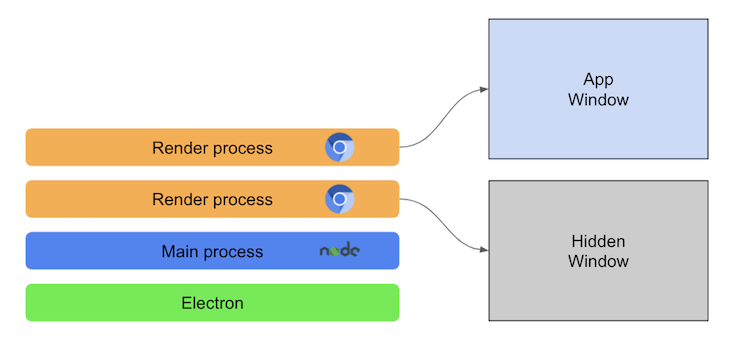
What security teams see:
- Chrome browser with constant CVE patches
- Node.js runtime with file system access
- Your app code running with system privileges
- No meaningful isolation between web content and system
The Audit Problem
Security auditors ask simple questions:
- "Why does your calculator need a web browser?"
- "How do you patch Chromium vulnerabilities?"
- "Can malicious web content access user files?"
The answers are bad:
- Because that's how Electron works
- Wait for Google to fix Chrome, then Electron to update
- Yes, that's the whole point
The CVE Treadmill
CVE-2023-44402 - ASAR integrity bypass on macOS. You could bypass integrity checks if you could write to the filesystem. Security team sent another "drop everything and patch this now" email.
CVE-2022-29247 - Renderers accessing ipcRenderer without validation. Not world-ending, but not good either. Lost a weekend figuring out which apps were vulnerable. Most of them, obviously.
This is the pattern: Electron's architecture creates these problems. It's not bugs getting fixed - it's the design that's fucked.
Why This Nightmare Continues
Electron gives web pages system access by design. The sandbox is optional and most apps disable it because shit breaks. Node.js integration means any HTML can spawn processes, read files, or hit your internal network.
I've been bitching about this for years. Security researchers keep finding new sandbox escapes. It's not bugs - it's the architecture that's broken.
That's why smart teams are switching to alternatives.



